Securing the MCP Gateway: Lasso Partners with Portkey to Deliver Enterprise-Grade Agentic AI Protection
Today, we’re excited to announce that Portkey and Lasso Security have partnered to provide AI Security directly into Portkey’s MCP Gateway - delivering real-time guardrails, threat detection, and governance enforcement at the protocol level.
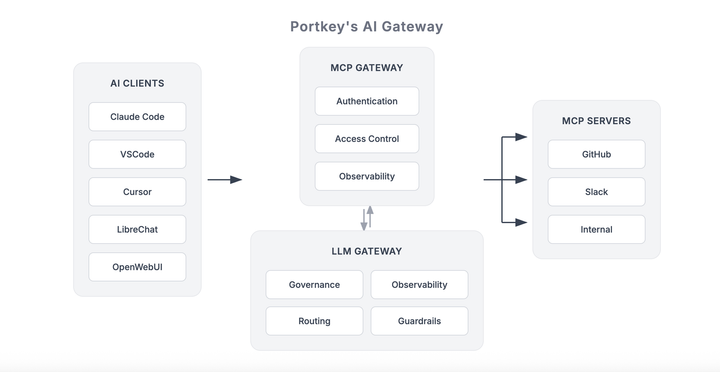
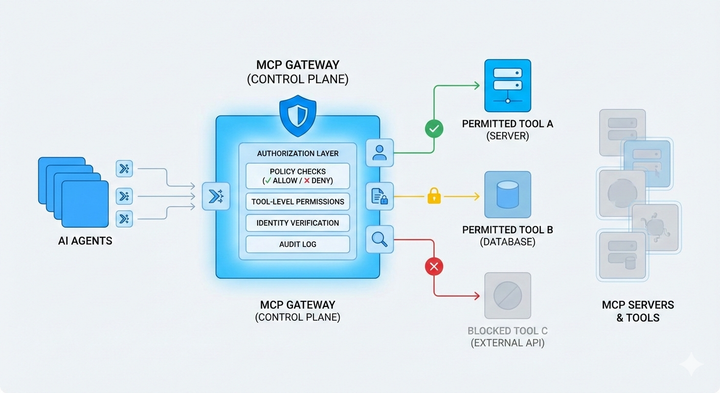
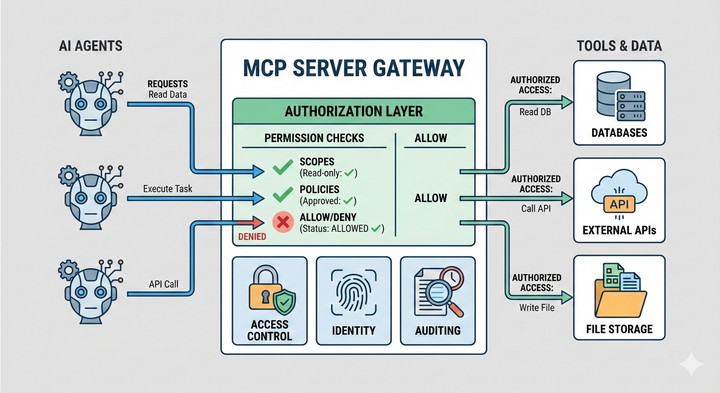
Portkey's MCP Gateway serves as the operational control plane for MCP deployments, centralizing authentication, authorization, and observability. It solves critical infrastructure challenges:
- Unified authentication across internal and third-party MCP servers
- Granular access control scoped to organizations, teams, and individual tools
- Centralized policy enforcement without redeploying agents
- End-to-end tracing correlating agent behavior with LLM activity
What the MCP Gateway provides in operational governance, Lasso now extends with runtime security intelligence, including:
The rise of MCP and its security implications
MCP has emerged as the de facto standard for connecting AI agents to external tools, data sources, and enterprise systems.
As organizations scale their agentic AI deployments, MCP enables the composability and interoperability that modern AI architectures demand.
But with great connectivity comes great risk.
MCP creates a new attack surfacem where a single compromised tool call can cascade across interconnected systems, where prompt injections can weaponize high-permission operations, and where misconfigured access controls can expose sensitive enterprise data. As AI agents gain autonomy, the stakes multiply.
How the integration works
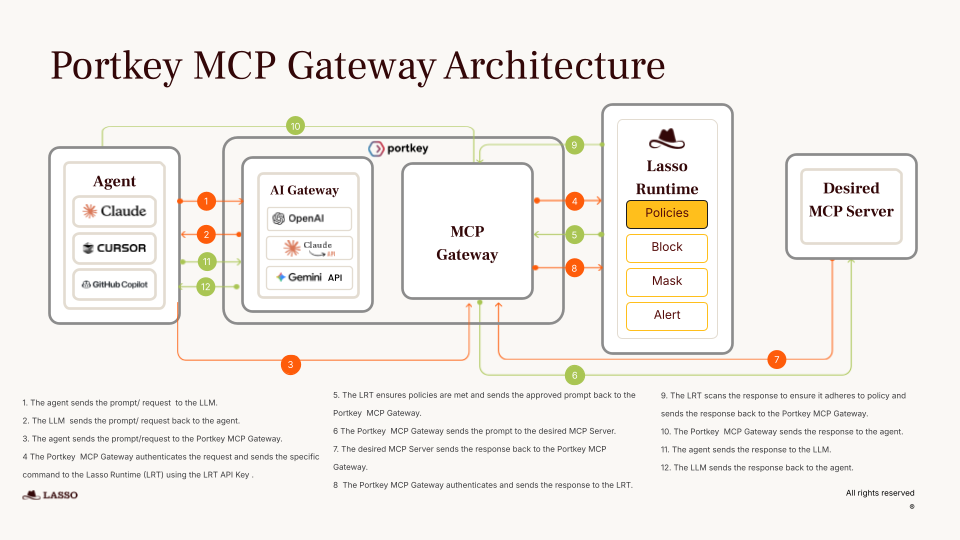
The Lasso-Portkey integration embeds Lasso's AI security engine directly into the MCP Gateway's request pipeline. Every tool call, every data exchange, and every agent-to-server interaction passes through Lasso's protection layer, with sub-50ms latency overhead.
Architecture overview
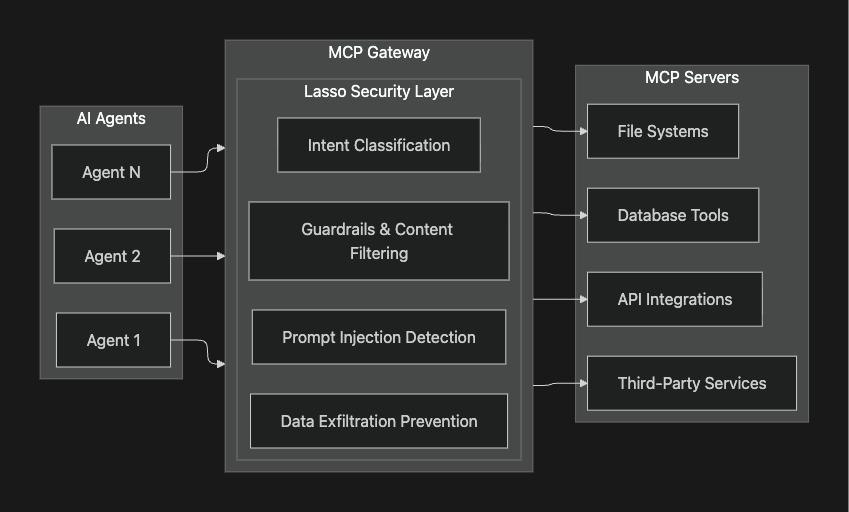
Security capabilities:
1. Prompt injection defense
MCP tool calls are prime targets for indirect prompt injection attacks. Malicious instructions embedded in retrieved data can hijack agent behavior, triggering unauthorized tool executions. Lasso's multi-layer detection analyzes both the content and context of every request, identifying adversarial patterns before they reach high-permission tools.
2. Intent-based access control
Traditional RBAC tells you what an agent can access. Lasso adds the WHY with an intent deputy that evaluates whether a tool call aligns with the agent'sstated objective and flags anomalous requests that may indicate compromise or misuse, even when permissions technically allow the action.
3. Cross-tool Data exfiltration prevention
In composable MCP architectures, data flows between multiple tools within a single agent workflow. Lasso monitors these inter-tool data movements, detecting patterns consistent with exfiltration attempts, such as sensitive data being passed to external communication tools or unauthorized storage endpoints.
4. Supply chain risk assessment
The MCP ecosystem includes third-party servers with varying security postures. Lasso provides continuous risk scoring for every MCP server in your registry, evaluating permissions requested, data handling practices, and behavioral patterns to surface supply chain vulnerabilities before they're exploited.
5. Real-Time Guardrails Enforcement
Apply behavioral guardrails uniformly across all agents traversing the gateway. Whether blocking PII exposure, enforcing compliance policies, or preventing risky tool combinations, Lasso's guardrails execute at wire speed, protecting without impeding legitimate operations.
Enterprise security challenges this partnership addresses
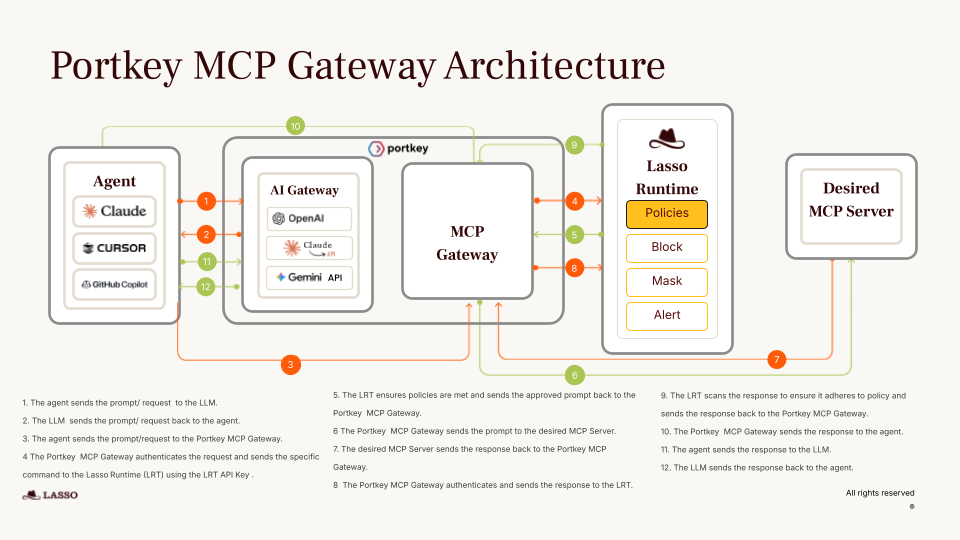
The shadow MCP problem
As teams independently deploy MCP servers to extend agent capabilities, security loses visibility. The Portkey and Lasso integration provides a unified discovery and protection layer every MCP server, every tool, and every agent interaction becomes visible and governable.
Non-deterministic agent behavior
AI agents don't follow predictable execution paths. The same prompt can trigger different tool sequences depending on context. Lasso's AI-native security models are purpose-built for this non-determinism, detecting threats based on behavioral intent rather than static signatures.
Compliance at scale
Enterprises operating in regulated industries need consistent policy enforcement across hundreds of agents and thousands of tool calls. The integrated solution applies compliance guardrails at the gateway level, ensuring no agent bypasses governance, regardless of which team deployed it.
What this means for security teams
This partnership delivers what enterprise security teams have been asking for: a single control point for MCP security.
Instead of instrumenting security into each agent, each MCP server, and each integration point, teams can now:
- Deploy once at the gateway and protect all downstream traffic
- Gain centralized visibility into agentic AI activity across the organization
- Enforce consistent policies without coordinating across development teams
- Detect threats in real-time with AI-native security models trained on 3,000+ attack patterns
For organizations already using Portkey's MCP Gateway, enabling Lasso requires no architectural changes as security activates at the configuration level.
Getting Started
The Lasso security layer for Portkey's MCP Gateway is available today for enterprise customers.
To enable the integration:
- Contact your Lasso representative or book a demo
- Configure your Portkey's MCP Gateway to route traffic through Lasso
- Define your security policies, guardrails, and alerting thresholds
- Monitor real-time threat intelligence through the unified dashboard
For existing Portkey customers, reach out to your account team to discuss enabling Lasso security on your MCP Gateway deployment.
The future of Agentic AI is secure
MCP is transforming how AI agents interact with enterprise systems. But protocol adoption without security consideration creates risk at scale.
Lasso ensures that as your agentic AI deployments grow, your security posture grows with them. Real-time protection, intent-awaredetection, and enterprise governance - delivered where it matters most: at the gateway.
Unlock the full potential of MCP. Securely.Request a Demo →
For technical documentation on the integration or partnership inquiries, contact [email protected].