What is shadow AI, and why is it a real risk for LLM apps
Unapproved LLM usage, unmanaged APIs, and prompt sprawl are all signs of shadow AI. This blog breaks down the risks and how to detect it in your GenAI stack.
Over the past year, LLMs have made their way into every corner of the enterprise, powering support chatbots, summarizing internal documents, and even helping teams write code, emails, or policies. But behind this excitement lies a growing, mostly invisible risk: Shadow AI
What is shadow AI?
Shadow AI refers to any use of AI models, APIs, or applications within an organization that occurs outside the visibility or control of central IT, security, or AI platform teams. This includes tools that are adopted without proper approval, model usage that isn’t monitored, or LLM features built into workflows without oversight.
In many ways, Shadow AI is the GenAI-era equivalent of Shadow IT, when employees started signing up for unauthorized SaaS tools before there were processes in place to govern cloud usage. The difference? Shadow AI has a much higher blast radius. A rogue spreadsheet might expose data; a rogue model could generate hallucinated, biased, or even unsafe content, all while costing your company real money.
Shadow AI doesn’t always start with bad intent, but with speed. Without governance, even good intentions can lead to serious risks.
Why shadow AI is rising
Shadow AI is the natural outcome of how fast LLMs and GenAI tools have evolved. The combination of low-friction APIs, open access to powerful models, and pressure to “do something with AI” has made it easier than ever for teams to bypass formal processes and ship quickly.
LLM APIs are easy to use. Anyone with an API key can call GPT-4, Claude, or open-source models in minutes, often without needing to involve infrastructure or security teams.
There’s a tool for everything. From Chrome extensions to no-code AI agents, GenAI tools are everywhere, and employees are using them to boost productivity, often without realizing the risks.
AI governance is lagging behind adoption. Many companies rushed to test GenAI but didn’t establish centralized controls, guidelines, or visibility mechanisms. The result is a fractured AI landscape.
Developer autonomy is high. Teams building GenAI features often move faster than the org can regulate. Without platform teams enforcing usage norms, model sprawl is inevitable.
It’s seen as experimentation. Early-stage projects often fly under the radar because they’re “just a test,” but in practice, these experiments often end up in production with no added safeguards.
Risks of shadow AI in production
Here are the key risks of shadow AI, especially when it leaks into production systems:
1. Security vulnerabilities
LLM APIs and tools used without approval often bypass standard security practices, no encryption, no API key management, no isolation of workloads. Sensitive customer data might be routed through unsecured endpoints or logged by third-party tools.
2. Compliance violations
If you're in a regulated industry, any uncontrolled AI use can break compliance, from using non-approved vendors to failing to retain logs for audits. Worse, employees may unknowingly share protected data (PHI, PII) with external models.
3. Reliability and debugging issues
Shadow AI apps often lack observability - no logs, no tracing, no error monitoring. When they fail, debugging is nearly impossible. And if they hallucinate or misbehave, no one may notice until the damage is done.
4. Budget and cost sprawl
Unmanaged API keys can rack up enormous bills without optimization or caching. Multiple teams might be duplicating the same LLM workloads across vendors, paying more for redundant usage.
5. Brand and reputational risk
If an external-facing feature powered by shadow AI generates hallucinated, offensive, or incorrect content, the brand takes the hit. And with no logs, it's hard to even prove what went wrong.
How shadow AI shows up in LLM apps
The problem with Shadow AI is that it slips quietly into production through a series of small, well-intentioned decisions, often made by developers or teams just trying to ship faster.
It might start with a developer grabbing an OpenAI API key and wiring it directly into a prototype, skipping centralized routing or authentication. That key often stays in use far beyond the pilot, silently driving production traffic without any cost tracking, access control, or rate limiting in place.
Meanwhile, the app itself might lack even basic observability. Prompts and responses aren't logged, which means teams have no way to debug issues or monitor model behavior. If the model hallucinates or outputs something unsafe, there’s no audit trail to trace the problem, let alone fix it.
Over time, different teams start solving similar problems independently. One team fine-tunes a model, another builds an agent workflow, and someone else copies a prompt from a blog post. There’s no shared prompt engineering standard, no versioning, no feedback loop. Model sprawl sets in, with multiple vendors and prompt styles scattered across the stack.
Often, what was meant as a harmless test gets embedded deeper into user-facing workflows. Suddenly, internal or customer data is flowing through systems with no security vetting and no SLAs. In some cases, teams even deploy autonomous agents that take actions (like responding to tickets or editing records) without ever involving the platform or security teams.
This is how shadow AI takes root. Not through malice or negligence, but through speed, fragmentation, and a lack of centralized visibility.
Detecting shadow AI starts with visibility. Most orgs don’t know it’s happening until something breaks or a large bill lands. Instead of waiting, teams should proactively scan for model usage across codebases, internal tools, and outbound API calls — especially in places not officially tracked, like prototypes or extensions.
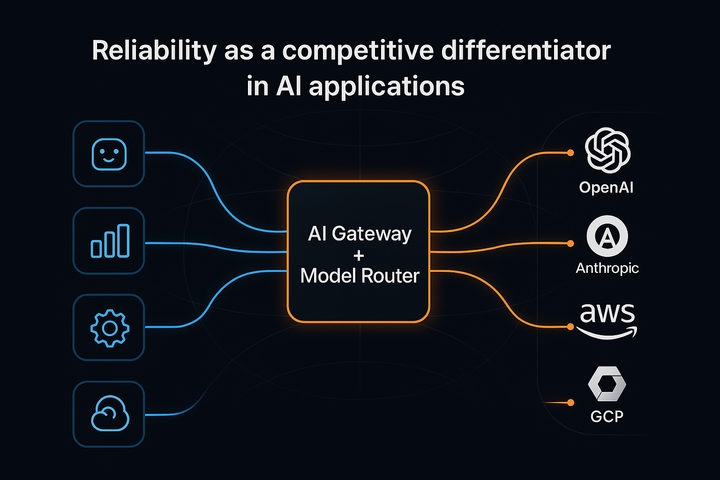
Once you’ve identified these touchpoints, the solution is to centralize. Routing all AI traffic through a single gateway gives you control over who’s using which model, what prompts are being sent, and how outputs are handled. This lets you enforce access controls, apply guardrails, and log everything for review and debugging.
It’s also important to put limits in place, like usage quotas, model whitelists, and budget alerts help prevent experiments from turning into costly risks. And for this to work at scale, the secure path needs to be fast. If your official AI infra is slow or clunky, teams will keep going around it.
An AI gateway like Portkey can help mitigate these risks by providing all these capabilities in a single platform.
Also read: Why enterprises need to rethink how employees access LLMs
Take the right action, soon
As more teams experiment with LLMs, the chances of unmanaged, unmonitored, and unapproved usage creeping into production grow rapidly. And with LLM outputs being non-deterministic and often high-stakes, even small leaks can cause serious damage.
The solution is to add visibility, control, and governance as early as possible. If you’re building with LLMs, assume shadow AI is already happening somewhere in your org. The sooner you identify and centralize usage, the easier it’ll be to keep your AI stack safe, scalable, and compliant.