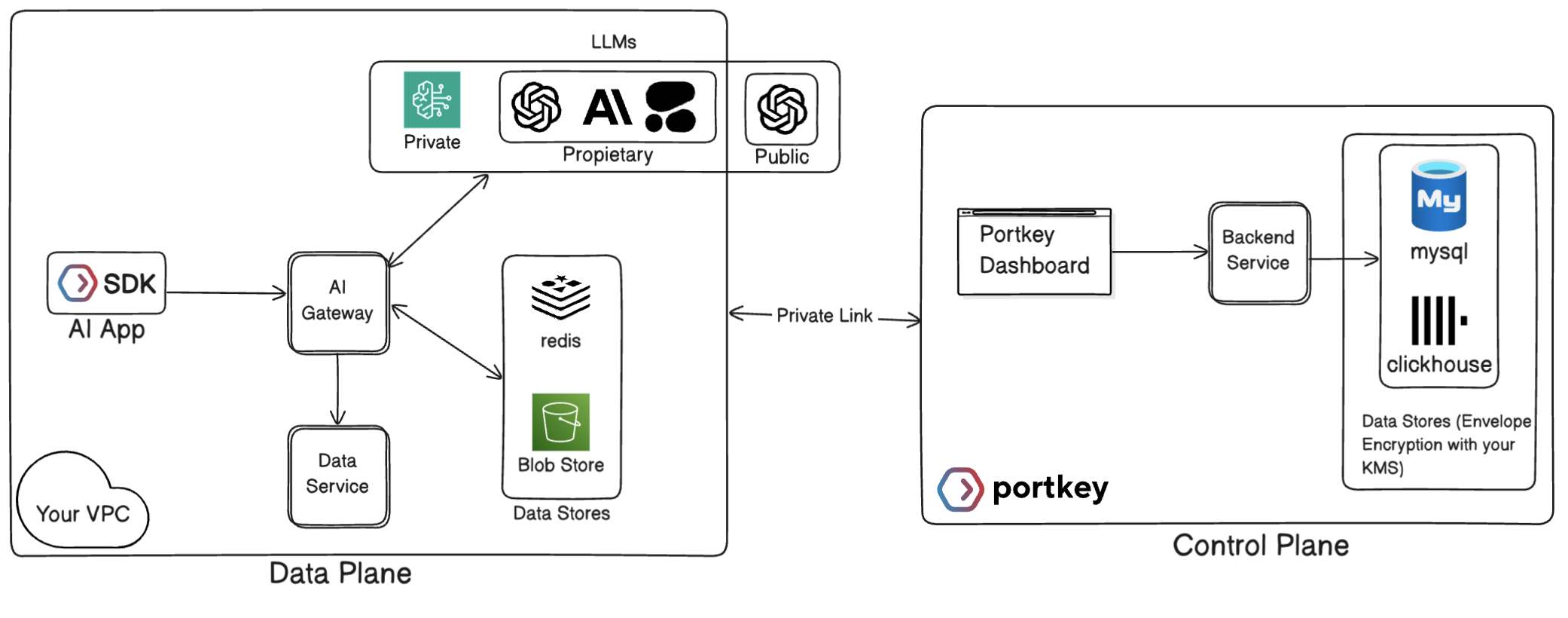
Hybrid Deployment Overview
Deploy a Hybrid Data Plane in 4 Steps
Step 1: Prepare Your Environment
1.1 Environment readiness
| Requirement | Notes |
|---|---|
| Kubernetes | v1.24+ (Helm 3.x) |
| Outbound HTTPS | Gateway must reach control.portkey.ai |
| Container Registry Access | Docker Hub / Portkey ECR for gateway image |
| Resource Sizing | CPU 1–2 cores, RAM 2–4 GB per Gateway |
| Storage | Depends on log retention (object storage or Mongo) |
1.2 Dependencies
| Component | Option A (auto) | Option B (bring-your-own) |
|---|---|---|
| Cache | Redis installed via Helm chart | External Redis/ElastiCache |
| Log Store | S3-compatible bucket (AWS S3, Wasabi, MinIO, GCS, NetApp) | MongoDB / DocumentDB |
Step 2: Obtain Credentials and Helm Repo
- Docker credentials – you’ll receive a 1Password link with
<docker-user>and<docker-pwd>. - Helm repo – add Portkey charts and create the registry secret:
Shell
Step 3: Configure values.yaml
Only a handful of parameters are required for a first-run. Start from the minimal template below and expand as needed.
values.yaml (minimal)

