Developer note: Most developers won’t add servers here. After an org admin provisions a server, use it from the workspace MCP page to copy the connection URL and test tools.
- Adding MCP servers (from catalog or custom URL)
- Configuring authentication for each server
- Viewing connection status and health metrics
- Controlling which teams access which servers
- Managing capabilities (tools, resources, prompts) per server
Quickstart
New to MCP Gateway? Add your first server in 5 minutes.
Adding Servers
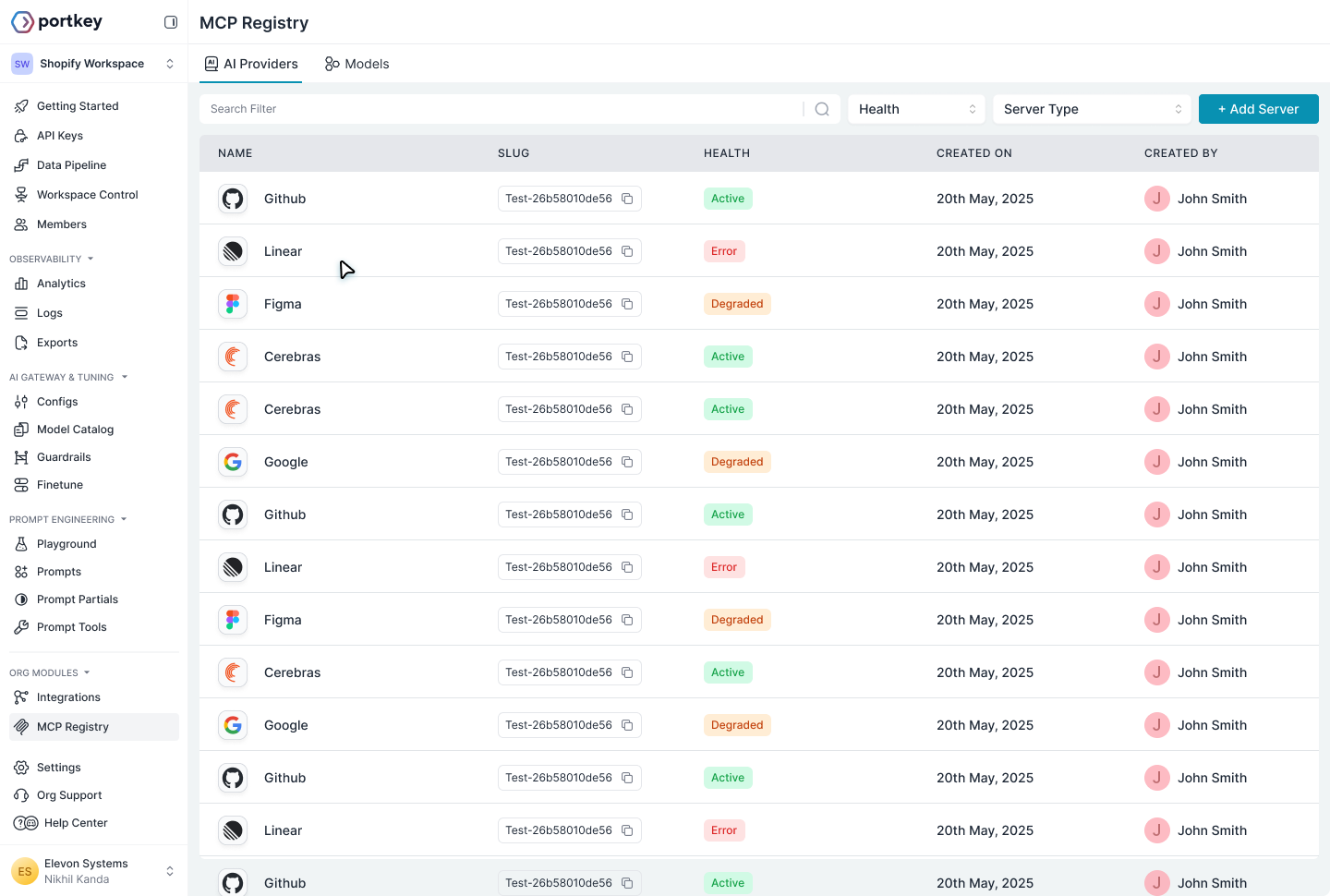
Click MCP Registry in the sidebar, then click Add MCP Server.| Field | Description |
|---|---|
| Name | Display name for the server |
| Slug | URL-friendly identifier (e.g., linear, internal-api) |
| Server URL | MCP endpoint (e.g., https://mcp.linear.app/mcp) |
| Server Type | HTTP for remote servers |
| Auth Type | Authentication method (see below) |
Portkey supports remote MCP servers over HTTP. Local STDIO servers need to be exposed as HTTP endpoints first.
Authentication
This section covers how Portkey authenticates to upstream MCP servers. For how your agents and MCP clients authenticate to Portkey, see Gateway Authentication.
| Auth Type | When to Use |
|---|---|
| None | Public servers with no authentication required |
| OAuth 2.1 | Servers with user-level OAuth. Each user gets their own tokens. |
| Client Credentials | Servers using OAuth client credentials. Shared across users. |
| Headers | Servers using API keys or static tokens. |
- OAuth (user-level): Each user authorizes their own access. Use for servers with user-specific data (Linear, GitHub, Slack).
- Client Credentials: Shared OAuth tokens. Use for service accounts or shared resources.
-
Headers: Static API keys sent with every request. Use for simple token-based auth.
Authentication Deep Dive
Gateway authentication, external OAuth, identity forwarding, JWT validation, and more.
Access Control
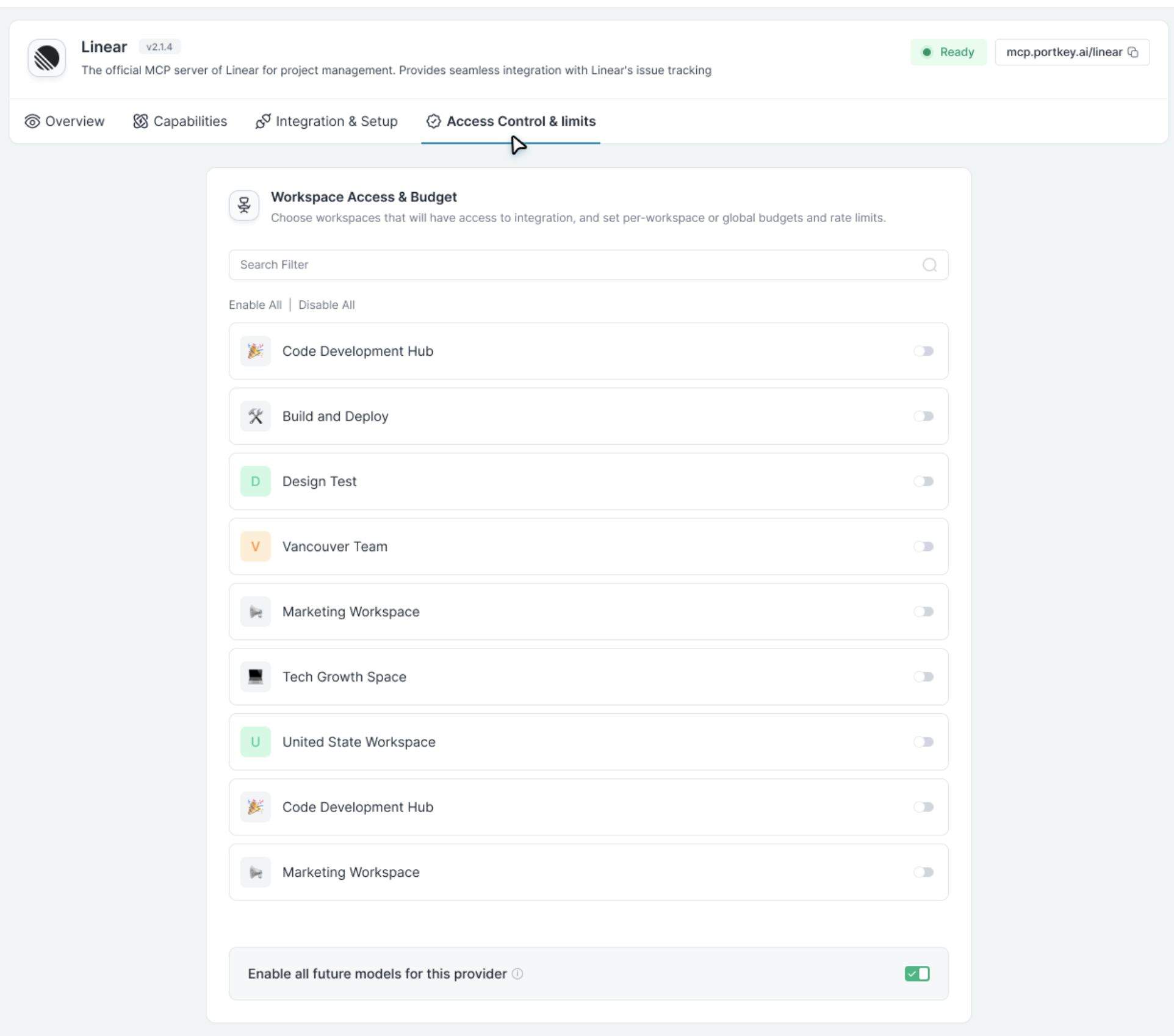
Access control for MCP servers happens at two levels.Organization-level (MCP Registry)
Requires Org Admin or Org Owner role.
- Click MCP Registry in the sidebar
- Click on an MCP server
- Open the Access Control tab
- Toggle workspaces on/off
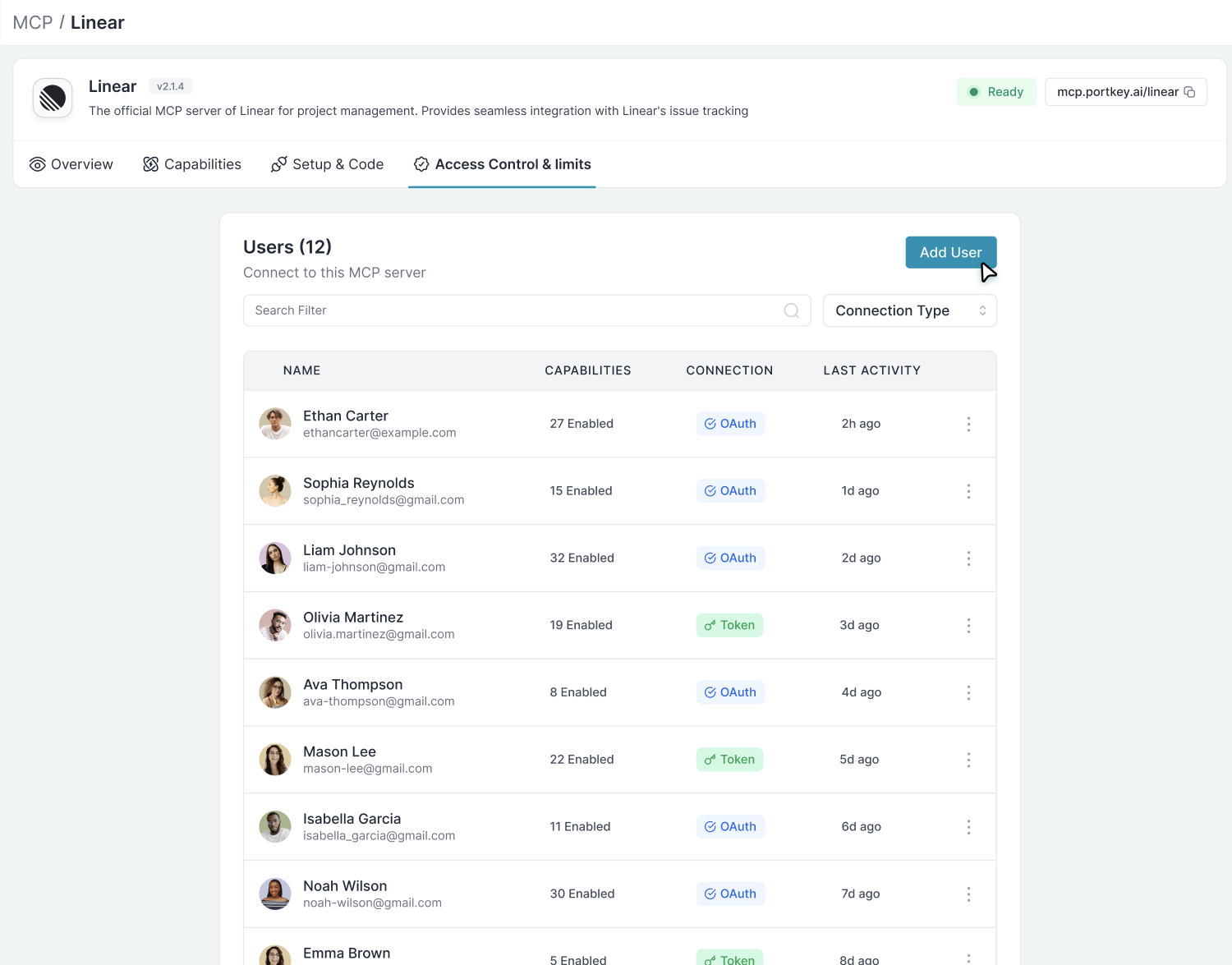
Workspace-level (MCP Servers)
Requires Workspace Manager or Workspace Admin role.
- Go to MCP page in your workspace sidebar
- Click on an MCP server
- Use the User Access tab to toggle user access on/off
Tool Provisioning
The Capabilities tab lists all tools, resources, and prompts exposed by an MCP server. Toggle them on or off, or use Enable All / Disable All for bulk changes.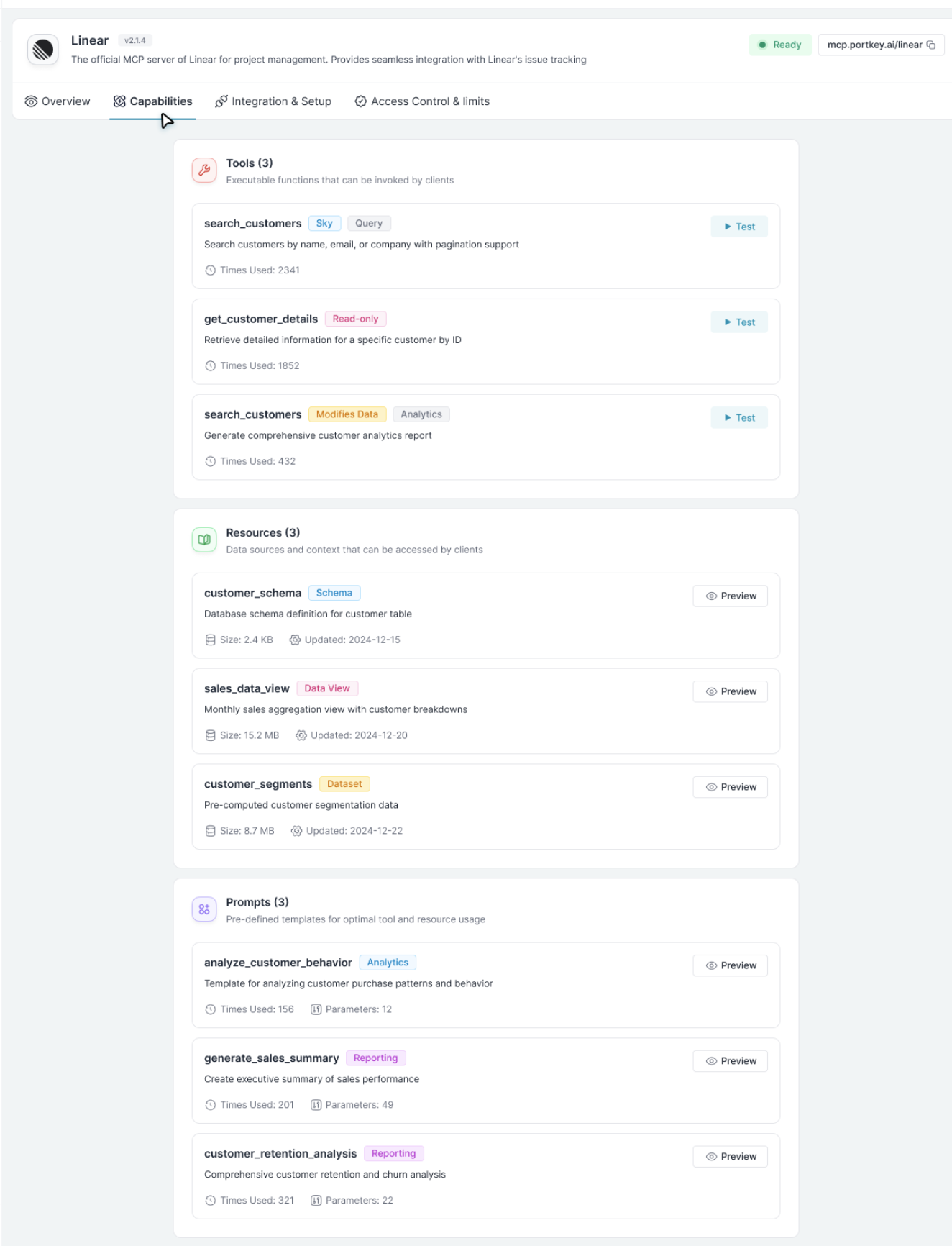
| Location | Who | Scope |
|---|---|---|
| MCP Registry → Server → Capabilities | Org Admins/Owners | Organization-wide |
| MCP Servers → Server → Capabilities | Workspace Managers/Admins | Workspace-only |
Server Overview
Once added, each server has a detail page with four tabs: Overview, Capabilities, Setup & Code, and Access Control & Limits.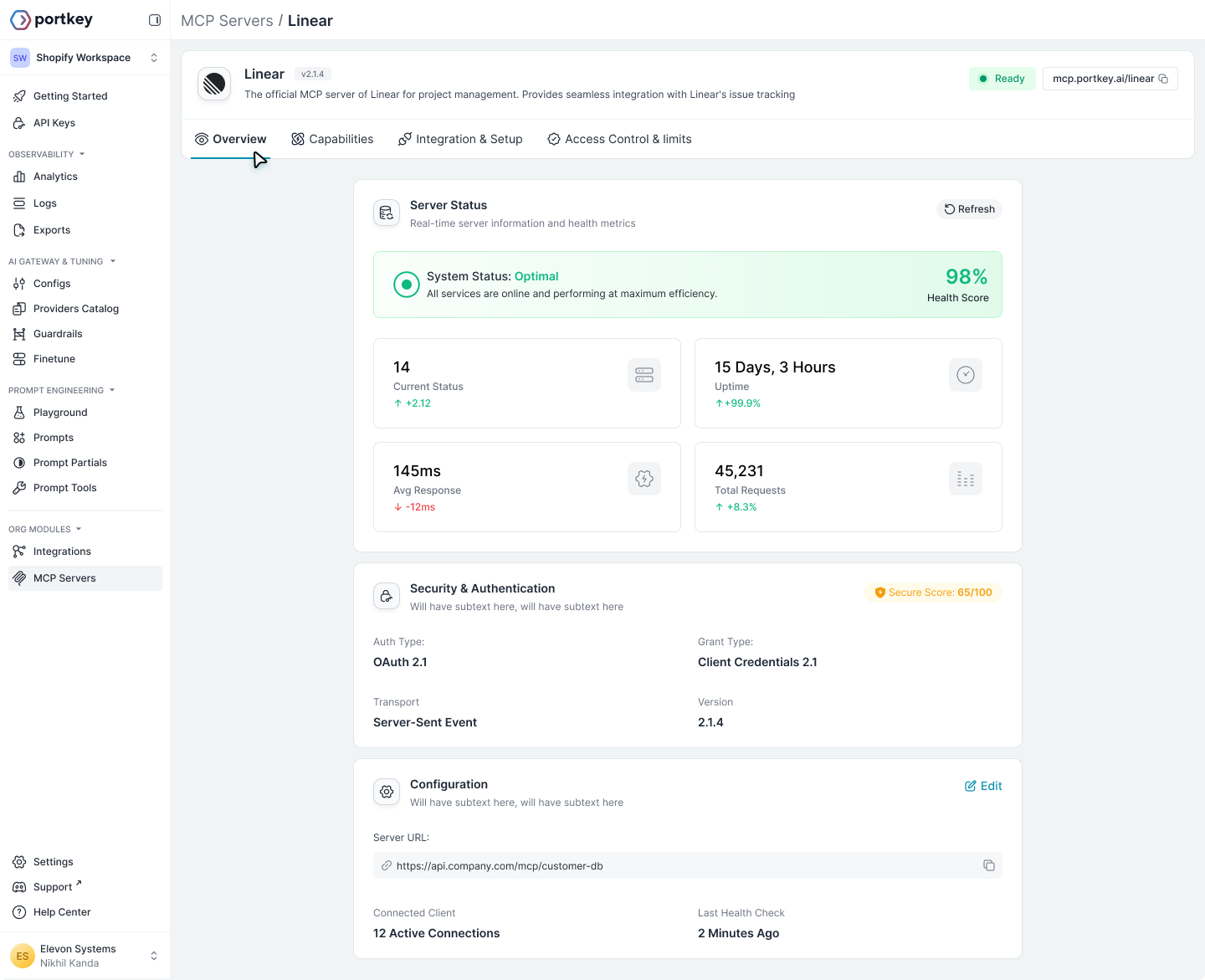
- Server Status: Health score, uptime, average response time, total requests
- Security & Authentication: Auth type, grant type, transport protocol
- Configuration: Server URL, version, connection details
Next Steps
Add Internal MCP Servers
Connect your own MCP servers with enterprise auth, access control, and logging.
Integrations
Setup guides for Claude Desktop, Cursor, Python SDK, TypeScript SDK, and more.
Observability
Monitor MCP traffic, debug issues, track usage.
Guardrails
Apply rate limits, content filtering, and approval workflows.

