This feature is available only on the Enterprise Plan of Portkey.
Validate JWT Token (Guardrail)
Validate your JWT Token before making a LLM request using Portkey.
Configuring JWT Authentication
JWT authentication can be configured under Admin Settings → Organisation → Authentication.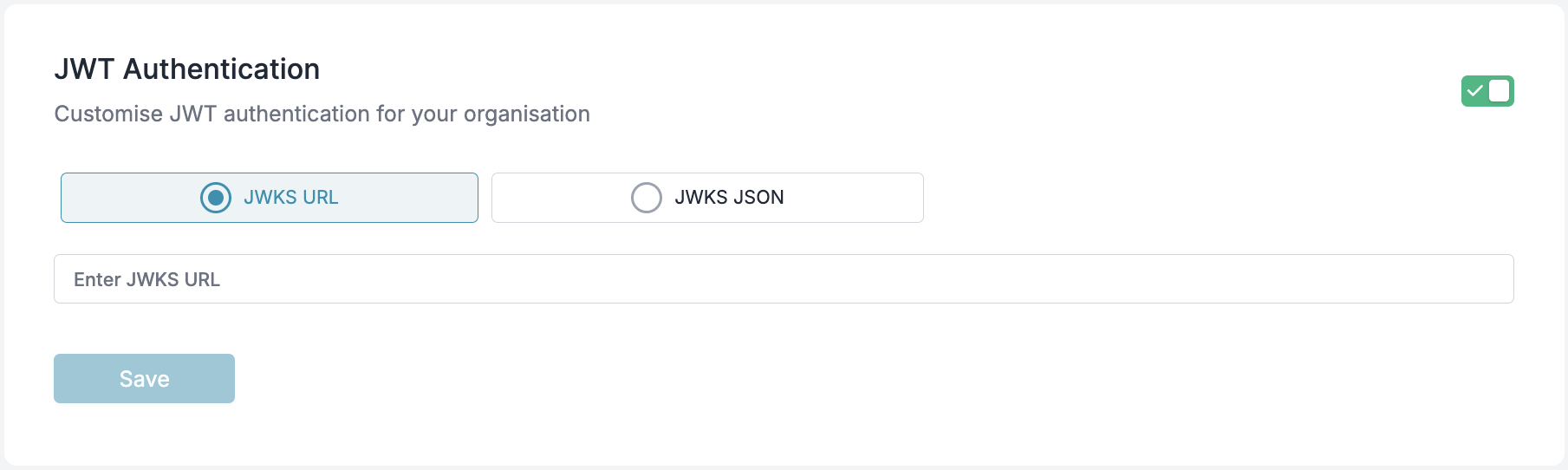
JWKS Configuration
To validate JWTs, you must configure one of the following:- JWKS URL: A URL from which the public keys will be dynamically fetched.
- JWKS JSON: A static JSON containing public keys.
Hard Requirements (Read First)
JWT Header (JOSE Header)
alg: Must beRS256. Symmetric algorithms likeHS256are not accepted.typ: Must beJWT.kid: Required. The value in the JWT header must match akidin your JWKS.
Key Requirements
- Key type: RSA
- Key size: 2048 bits or higher
- Your JWKS must expose only the public key parameters (e.g.,
kty,n,e,use,alg,kid). Do not include private key material.
JWT Requirements
Supported Algorithm
- JWTs must be signed using RS256 (RSA Signature with SHA-256).
Required Claims
Your JWT payload must contain the following claims:| Claim Key | Description |
|---|---|
portkey_oid / organisation_id | Unique identifier for the organization. |
portkey_workspace / workspace_slug | Identifier for the workspace. |
scope / scopes | Permissions granted by the token. |
exp | Expiration time (as a UNIX timestamp, in seconds). |
expis mandatory. Tokens withoutexpor with expiredexpare rejected.iatand/ornbfare recommended but optional.
Optional Claims
| Claim Key | Description |
|---|---|
defaults | Object containing default settings applied to all requests made with this token. See Embedding Default Configs below. |
usage_limits | Usage limits to enforce on requests made with this token. |
rate_limits | Rate limits to enforce on requests made with this token. |
User Identification
Portkey identifies users in the following order of precedence for logging and metrics:email_idsubuid
End-to-End Working Example (Generate → Configure JWKS → Sign → Call)
The following example uses Node.js and thejose library to:
- generate an RSA key pair,
- create a JWKS containing the public key,
- sign a JWT with the private key,
- call Portkey with the JWT.
1) Prerequisites
2) Generate RSA Keys, Create JWKS, and Sign a JWT (NodeJS)
Creategenerate-and-sign-jwt.mjs:
jwks.json: A JWKS containing your public key (with akid).token.jwt: A signed JWT ready to use with Portkey.
3) Add Your Public Key to Portkey (JWKS)
In the Portkey Admin UI:- Navigate to Admin Settings → Organisation → Authentication.
- Choose either:
- JWKS URL: Host
jwks.jsonat a reachable HTTPS URL and paste that URL. - JWKS JSON: Paste the entire contents of your generated
jwks.json.
- JWKS URL: Host
- Save changes.
kid in your JWT header matches a key in the configured JWKS.
4) Call Portkey Using the Signed JWT
Send the JWT in thex-portkey-api-key header.
If you prefer Python for signing, you can generate the RSA key pair using your preferred method, ensure the public key is present in your JWKS with a matching
kid, and use a library like PyJWT to sign with RS256 while setting the header { "alg": "RS256", "typ": "JWT", "kid": "<your-kid>" }.Authentication Process
-
The client sends an HTTP request with the JWT in the
x-portkey-api-keyheader: -
The server validates the JWT:
- Verifies the signature using the JWKS.
- Checks if the token is expired.
- Ensures the required claims are present.
- If valid, the request is authenticated, and user details are extracted for authorization and logging.
- If invalid, the request is rejected with an HTTP 401 Unauthorized response.
Authorization & Scopes
Once the JWT is validated, the server checks for the required scope. Scopes can be provided in the JWT as either a single string or an array of strings using thescope or scopes claim.
Scopes can also be prefixed with portkey. (e.g., portkey.completions.write).
JWT tokens with appropriate scopes function identically to workspace API keys, providing access to workspace-specific operations. They cannot be used as organization API keys, which have broader administrative permissions across all workspaces.
Example JWT Header
- This matches the signing example (
.setProtectedHeader({ alg: 'RS256', kid: publicJwk.kid, typ: 'JWT' })). - Ensure
kidexactly matches one key in your configured JWKS.
Embedding Default Configs in JWT
You can embed a default config directly in the JWT payload using thedefaults claim. This works the same way as attaching default configs to API keys, but lets you control it per-token — useful when different users or services need different routing rules.
The defaults object supports the following fields:
| Field | Description |
|---|---|
config_id | The ID of the config to apply as the default for all requests made with this token. |
metadata | A JSON object with custom metadata to attach to all requests. |
defaults.config_id is used, Portkey validates that the config belongs to the same organization before applying it. If the config is not found or doesn’t belong to the org, the default is ignored.
This follows the same precedence rules as API key default configs — if a user explicitly passes a config ID in their request headers, it will override the JWT default unless config override is disabled at the workspace level.
Example JWT Payload with Defaults
Example JWT Payload
Making API Calls with JWT Authentication
Once you have a valid JWT token, you can use it to authenticate your API calls to Portkey. Below are examples showing how to use JWT authentication with different SDKs.- NodeJS
- Python
- cURL
- OpenAI Python SDK
- OpenAI NodeJS SDK
Install the Portkey SDK with npm
Troubleshooting “Invalid API Key” Errors
- Wrong algorithm: Only
RS256is accepted;HS256or others will fail. - Missing or mismatched
kid: Your JWT header must include akidthat matches a key in the JWKS. - Incorrect header usage: Send the raw JWT in
x-portkey-api-keywithout aBearerprefix. - Expired or missing
exp: Theexpclaim is required and must be in the future. Allow for small clock skew. - Private vs Public key mix-up: Your JWKS must contain only the public key parameters. The private key is used only for signing; never paste it into the JWKS JSON.
- Wrong org/workspace identifiers:
portkey_oid(ororganisation_id) andportkey_workspace(orworkspace_slug) must correspond to valid identifiers in your Portkey tenant. - Scopes missing for the API you call: E.g., chat completions needs
completions.write. - Unreachable JWKS URL: If using a URL, it must be publicly reachable by Portkey. For static JSON, ensure the pasted JSON is valid and includes
keys: [...].
All Invalid JWT errors are logged in the Audit Logs.
Sample error message:
Caching & Token Revocation
- JWTs are cached until they expire to reduce validation overhead.
- If you rotate keys:
- Publish the new public key in JWKS with a new
kid. - Start issuing tokens signed by the new private key (with the new
kid). - Old tokens will remain valid until their
expis reached.
- Publish the new public key in JWKS with a new

