Using a Private MCP Server? If your MCP server is behind a firewall, on localhost, or not publicly accessible, the model provider won’t be able to reach it. Check out our guide on Using Private MCP Servers to learn how to handle tool fetching and invocations on the client side.
OpenAI Responses API Remote MCP Support
A Responses API request to OpenAI with MCP tools enabled.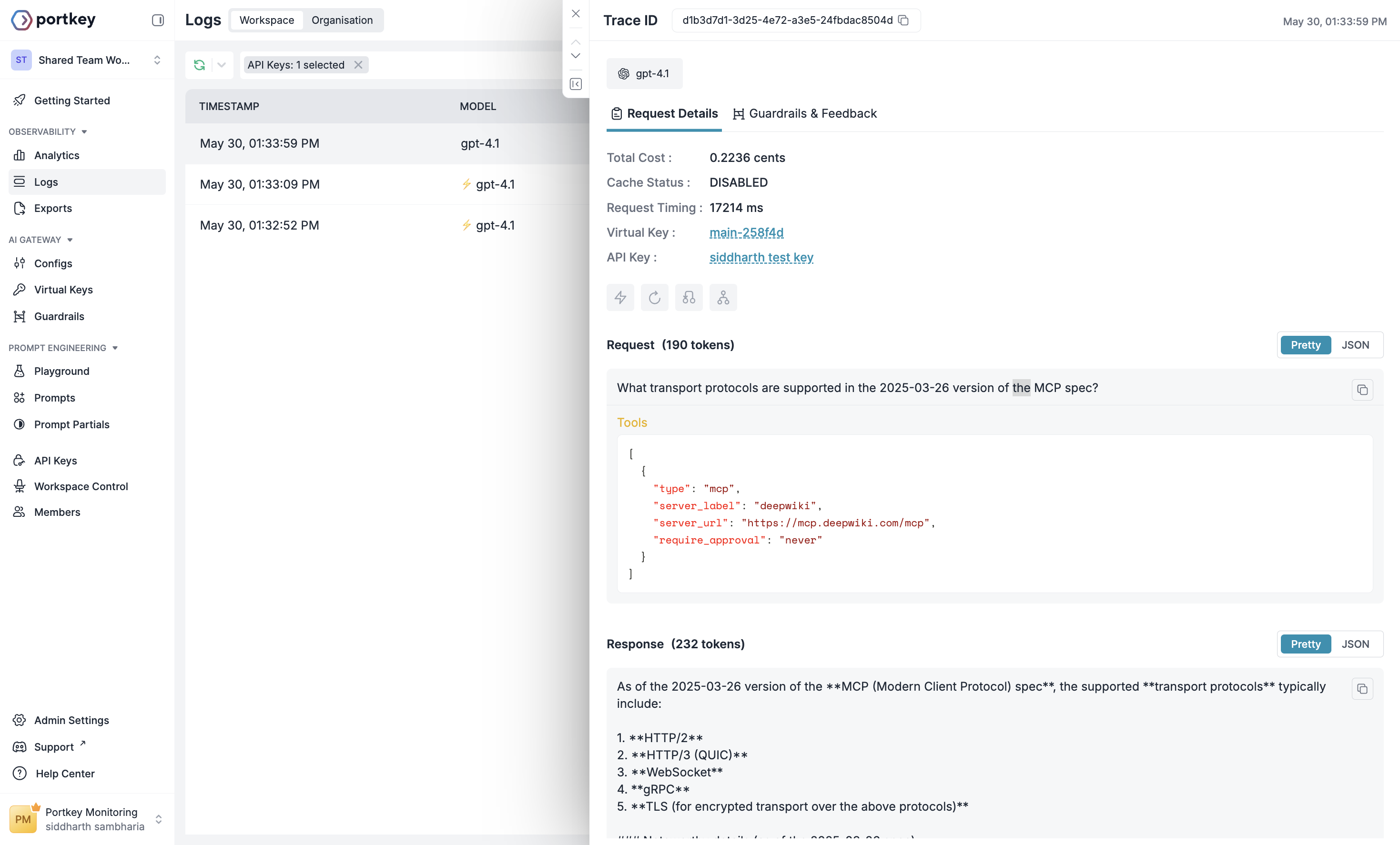
MCP Server Authentication
Unlike the DeepWiki MCP server, most other MCP servers require authentication. The MCP tool in the Responses API gives you the ability to flexibly specify headers that should be included in any request made to a remote MCP server. These headers can be used to share API keys, oAuth access tokens, or any other authentication scheme the remote MCP server implements. The most common header used by remote MCP servers is theAuthorization header. This is what passing this header looks like:
Use Stripe MCP tool
headers object. These values will also not be visible in the Response object created. Additionally, because some remote MCP servers generate authenticated URLs, we also discard the path portion of the server_url in our responses (i.e. example.com/mcp becomes example.com). Because of this, you must send the full path of the MCP server_url and any relevant headers in every Responses API creation request you make.
Anthropic’s Messages API MCP connector
Claude’s Model Context Protocol (MCP) connector feature enables you to connect to remote MCP servers directly from the Messages API without a separate MCP client.This feature requires the beta header:
"anthropic-beta": "mcp-client-2025-04-04"- Direct API integration: Connect to MCP servers without implementing an MCP client
- Tool calling support: Access MCP tools through the Messages API
- OAuth authentication: Support for OAuth Bearer tokens for authenticated servers
- Multiple servers: Connect to multiple MCP servers in a single request
Using the MCP connector in the Messages API
To connect to a remote MCP server, include themcp_servers parameter in your Messages API request:
mcp_servers array supports the following configuration:
Field descriptions
| Property | Type | Required | Description |
|---|---|---|---|
type | string | Yes | Currently only “url” is supported |
url | string | Yes | The URL of the MCP server. Must start with https:// |
name | string | Yes | A unique identifier for this MCP server. It will be used in mcp_tool_call blocks to identify the server and to disambiguate tools to the model. |
tool_configuration | object | No | Configure tool usage |
tool_configuration.enabled | boolean | No | Whether to enable tools from this server (default: true) |
tool_configuration.allowed_tools | array | No | List to restrict the tools to allow (by default, all tools are allowed) |
authorization_token | string | No | OAuth authorization token if required by the MCP server. See MCP specification. |
Response content types
When Claude uses MCP tools, the response will include two new content block types:MCP Tool Use Block
MCP Tool Result Block
MCP Server Authentication
For MCP servers that require OAuth authentication, you’ll need to obtain an access token. The MCP connector beta supports passing anauthorization_token parameter in the MCP server definition.
API consumers are expected to handle the OAuth flow and obtain the access token prior to making the API call, as well as refreshing the token as needed.
Obtaining an access token for testing
The MCP inspector can guide you through the process of obtaining an access token for testing purposes.-
Run the inspector with the following command. You need Node.js installed on your machine.
- In the sidebar on the left, for “Transport type”, select either “SSE” or “Streamable HTTP”.
- Enter the URL of the MCP server.
- In the right area, click on the “Open Auth Settings” button after “Need to configure authentication?”.
- Click “Quick OAuth Flow” and authorize on the OAuth screen.
- Follow the steps in the “OAuth Flow Progress” section of the inspector and click “Continue” until you reach “Authentication complete”.
-
Copy the
access_tokenvalue. -
Paste it into the
authorization_tokenfield in your MCP server configuration.

